Login and Two-Step Authentication FAQ
Logging in
I forgot my password. How can I log in?
Go to the Stanford University Accounts webpage and click the Forgot password? button, then follow the steps to reset your password.
Why am I getting "are you logging in" messages when I'm not trying to log in?
If these are push-based Duo authentication prompts (i.e., Duo Push, SMS text, or Phone Call), then this could be an indication that an adversary has obtained your SUNet ID password and is attempting to log in as you. Two-step authentication is doing its job, and you should never approve an authentication prompt that you did not initiate or for which you cannot identify the source. See below for what to do about potential password compromise.
This could also be the result of an application/service that you previously logged into encountering a session timeout. If the application can access a valid credential (such as a Cardinal Key certificate or cached Windows domain credential) that satisfies the SUNet ID password requirement but still requires two-step, then it will initiate a prompt on your behalf to restore the session. Some applications (i.e., NetDB, RegAdmin, self-service password reset) always require two-step authentication. Also, if you clicked the “Yes, trust browser” option in that device’s web browser, exceeding 90 days will cause the browser to prompt for two-step if you are logged in to Google Drive or any other web-SSO application. If you cannot determine the source of these prompts, see below for what to do.What should I do if I suspect my SUNet ID password might be compromised?
If you are receiving Duo prompts that you did not initiate, you should change your password as soon as possible. Most password compromises are the result of database breaches or successful phishing attacks, so it should not be taken as an indication that your local computer is also compromised. However, if you have any reason to suspect the computer you are working on is also compromised, please use a different computer to change your password.
What if I have changed my SUNet ID password and I am still receiving Duo prompts that I did not initiate?
If the uninitiated Duo prompts still continue after you change your SUNet ID password (and it is unlikely the adversary could have obtained your new password), then it is more likely the result of some application attempting to recover from a session timeout on your behalf. Please restart your computer and any other remote sessions that you may have logged into. This should terminate the responsible session and allow you to approve any authentication prompts with confidence.
What should I do if I suspect that I may have entered my SUNet ID password and Duo Mobile passcode into a malicious website?
Change your password as soon as possible using these instructions. Use your Duo Mobile passcode to two-step authenticate, as this will invalidate the previous passcode that was compromised.
Why am I being prompted for my passcode when I usually use Duo push?
Regardless of what method Duo normally presents you, if you are presented with a two-step prompt where passcode is the only option, you should be wary. This is the most common method adversaries use to obtain your two-step credential (after previously collecting your SUNet ID password). You should cancel this session and double check the authenticity of the application link you are using.
Additionally, with Duo Universal Prompt, it is no longer possible to select a default authentication method, like Duo Push, for all future two-step authentications. Instead, Duo will present you with the most secure out of the methods available to you. You may click Cancel and choose Other Options, which will then be presented to you next time (as the last authentication method from this device/browser combination).I used to receive Duo authentication prompts after entering my SUNet ID password, but now I am able to log in without two-step authentication.
Two-step authentication is always required after SUNet ID password authentication because a password is considered a weak form of authentication that is easily compromised. Cardinal Key is a stronger form of certificate-based authentication that some applications (i.e., Cardinal Key based VPN) deem to be sufficient, so no additional two-step authentication is required. Some highly sensitive applications (i.e., NetDB, RegAdmin, self-service password reset) will always prompt for two-step authentication even after Cardinal Key authentication.
This may also be because you are logging in with the same device/browser combination where you clicked the “Yes, trust browser” option. If so, the browser will automatically remember you, and you will not be prompted to authenticate for that application or service for the next 90 days.Why are Duo Mobile passcodes no longer sufficient?
The Duo Mobile passcode remains valid until it, or a subsequently-generated passcode, is used. They are vulnerable to phishing attacks that are intricately designed to steal them before they expire, thus allowing malicious users to gain access to systems and user data. If you use Duo Mobile passcode, you should switch to a more secure authentication option, such as Duo Mobile Push, or use a security key. After Feb. 23, 2023, the Duo Mobile Passcode authentication method will be disabled.
Using two-step authentication devices and methods
What is the recommended two-step authentication method?
If you can authenticate with a smartphone or tablet, Duo Push is the recommended method; it is quick, simple, and secure.
How can I use two-step authentication without a smartphone?
Authentication with a security key does not require an internet connection, cellular connection, or separate device. A security key can be ordered and self-enrolled by following these instructions. Tokens are available from the Stanford ID Card office.
You can also authenticate by a call to a mobile phone or a call to a landline.
My device does not have an internet or cellular connection when I travel. How can I use two-step authentication?
You can authenticate with the Duo Mobile app passcode, which requires a device but does not require an internet or cellular connection.
My default two-step authentication device has changed. How do I reset it?
The new prompt does not offer a way to configure a default authentication device (see "Universal Prompt" on the Duo support webpage). Therefore, you can no longer set a default authentication method by navigating to accounts.stanford.edu and selecting the "Two-Step Management" tile.
Instead, you will always be prompted for your last-used authentication method. If you select an option and authenticate with it, you will automatically be prompted with it until you authenticate with a different method. To choose a different authentication method from what is initially provided in the prompt, select “Other options."
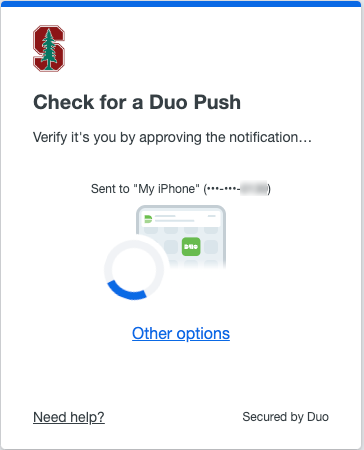
How do I change my default two-step authentication device?
The new prompt does not offer a way to configure a default authentication device (see "Universal Prompt" on the Duo support webpage). Therefore, you can no longer set a default authentication method by navigating to accounts.stanford.edu and selecting the "Two-Step Management" tile.
Instead, you will always be prompted for your last-used authentication method. If you select an option and authenticate with it, you will automatically be prompted with it until you authenticate with a different method. To choose a different authentication method from what is initially provided in the prompt, select “Other options."

How can I get a security key for two-step authentication?
Purchase your choice of Yubikey and self-enroll it as a security key.
Can I use a printed list to authenticate?
You can no longer request a printed list for two-step authentication.
If you use a printed list for two-step authentication, choose one of these simple and reliable alternatives:
- If you can authenticate with a smartphone or tablet, Duo Push is the recommended method; it is quick, simple, and secure.
- Use the Duo Mobile app passcode, which requires a device but does not require an internet or cellular connection.
- If you need to authenticate without an internet connection, cellular connection, and/or a smartphone or tablet:
- A security key can be ordered and self-enrolled by following these instructions.
- Use a call to a mobile phone or a call to a landline (not recommended).
Can I use SMS (text message) to authenticate?
University IT does not recommend using SMS for two-step authentication, because the National Institute of Standards and Technology (NIST) has reported that SMS authentication is less secure than other two-step authentication options. If you authenticate using SMS, consider changing to Duo Push. This recommended method is quick, simple, and secure. You can review other ways to authenticate on the Two-Step Authentication website.
I self-enrolled my YubiKey as a Security key, but need to two-step authenticate for Shell Access and other non-web based services. How can I get my YubiKey to prompt for a YubiKey passcode?
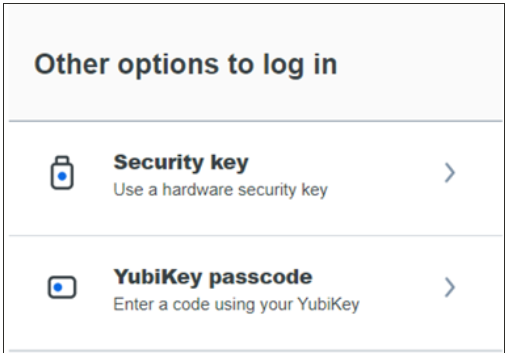
Firstly, ensure that your YubiKey can be programmed with a passcode, such as the YubiKey 5 Series. Then submit a HelpSU ticket requesting passcode programming for an existing YubiKey. A trained Duo administrator will schedule a working session to assist you.
Troubleshooting two-step authentication
I lost my two-step authentication device and don't have access to a backup device. How can I use two-step authentication?
You can generate a one-time bypass code on the Stanford University Accounts webpage using your University ID card and the answer to your password reset question.
I'm setting up a two-step authentication device but I want to cancel the setup. How do I cancel it?
It is a known Duo bug that there is no option to cancel the device setup process. We have reported this to Duo. As a workaround, you can close the browser window and navigate back to the site to stop the setup process.
Why was I not asked to do legacy two-step authentication with web.stanford.edu?
Starting December 2023, duplicate multiple-factor authentication will be retired. See "How to Fix Two-Step Authentication Issues with WebAuth Websites" for more details.
My two-step authentication content does not load. What should I do?
If the two-step authentication content does not load, try disabling your ad blocker or third-party browser extensions.
My browser does not auto-fill the login address. What should I do?
If your browser doesn't auto-fill, it may be because you use a password manager. Login.stanford.edu uses a new URL so you need to re-enter your username and password in the password manager.
