This page is for everyone at Stanford University, Stanford Health Care (SHC), and Stanford Medicine Children’s Hospital (SMCH) with access to sensitive data, including health care data and protected health information (PHI).
YOU are responsible for taking precautionary measures to protect any data you use, access, or share at Stanford.
Quick help needed? Grab the infographic:
Click the image to see full-size version
Why is protecting sensitive data so important?
Our commitment
Stanford is committed to privacy and data security.
This commitment is important for everyone in the Stanford community to adopt for the protection of our people and our information, especially related to health care data.
Legal requirements and consequences
Consequences for mishandling data can include fines (for Stanford or you), imprisonment, and loss of your professional license.
Privacy and data security laws include serious consequences for failing to protect confidentiality and security–for both Stanford and for you as an individual.
Impact for others
Let's not forget the reason for our commitment—the potential impact for those who we are trying to protect, like patients and clinical trial participants.
Risks of mishandling sensitive data include:
- Identity theft and fraud
- Stigma and discrimination
- Compromised healthcare due to mishandled data
- Loss of trust in healthcare services, negatively affecting healthcare
- Financial and legal consequences for costs related to resolving issues
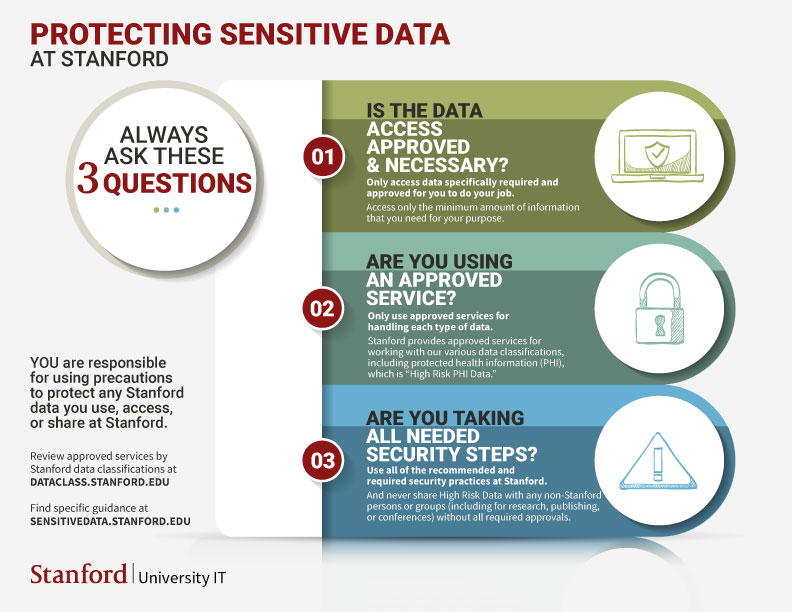
Three questions to help you protect sensitive data
Open each section to see details.
When it comes to accessing (including querying) data, there is a significant difference between what you can access and what you should access.
For example, employees have access to operational and/or clinical systems with data based on their role within the organization and business need for access. That encompasses that data an employee can access.
However, employees should access only what is specifically required and approved.
Approved
- ONLY access data or run reports for functions and projects that have been approved for you to work on.
- ONLY for the purpose to support internal operations and improvement purposes; access for other purposes is prohibited unless authorized by the relevant privacy authority.
Necessary
- ONLY data specifically required for you to do your job at Stanford. (This is the "need to know" principle.)
- ONLY the minimum amount of information or data that you need to accomplish your intended purpose. (This is the "minimum access" principle.)
NOT approved
- High Risk Data should not be used for research, publishing, conferences, or any other sharing with external parties without approval from relevant privacy authorities.
- Never share High Risk Data with non-Stanford individuals or groups without all required approvals.
Only use approved services for the data which you are accessing or using.
The Stanford data classification for PHI is “High Risk PHI Data.” There are approved services for handling this type of data.*
*Note that any solution(s) for High Risk PHI might have special processes and procedures also required in order to ensure data privacy and security. Be sure to review all of the related requirements. Seek assistance or request a data risk assessment (DRA).
Critical security steps
- Your access credentials to Stanford applications and data have been granted solely for your use. Never share your access credentials (login IDs and passwords) with anyone. You will be held responsible for any activity that occurs using your login ID.
- Use a strong password.
- Only use Stanford-approved encrypted devices to access, capture, store or transmit confidential data.
- Lock or secure workstation when walking away from your workstation.
- SHC/SMCH Employees, specifically:
- Store data on the SHC/SMCH secured network.
- Use Secure email.
- Use Stanford Medicine Box or remote access to store and transfer files.
- Engage IT for secure external file transfers.
- Assume all data requires protection under the law unless it is properly de-identified. There are specific legal requirements for information to be considered de-identified under the law. Contact the Privacy Office for direction on how to de-identify information.
- These are just some of the top tips for security. Check out more security guidance.
Required documentation for accessing patient information
- You must maintain complete and accurate documentation for each project for which you access or query data applications containing patient information.
- Documentation must be maintained for six (6) years.
- Documentation must include the name & purpose of the project, data fields required for the project, date range of project, sample reports, and executive sponsor.
- Documentation can be in the form of a log (spreadsheet) or project plan/charter.
- Reports (both electronic and paper) produced as a result of the project must include:
- Project Name
- Date
- Name of individual who created report
- Statement “For internal SHC (or SMCH as appropriate) business purposes only”
Important facts on protecting sensitive data
Keep in mind that various protections and consequences apply for specific types of data and situations.
Let's look at a few details:
Proprietary sources
Data received from a proprietary source (such as corporate data or information about sponsored research projects) can be sensitive and require protection from disclosure.
State laws and other geographically based laws
The State of California has its own legal requirements for different types of sensitive data, as do other states.
GDPR (General Data Protection Regulation)
Data subject to European Union privacy regulations (GDPR) must be treated as sensitive personal information even if coded (where HIPAA allows de-identified data to retain certain types of codes).
Individually-identifiable data
Data that are individually identifiable (such as SSNs) but not created or maintained by a HIPAA-covered entity (such as a hospital) may not be subject to HIPAA but may be subject to other legal or contractual restrictions.
Research subject to IRB approval
For research subject to IRB approval, data management is governed by the terms of that IRB approval, which may be more limiting or specific that Stanford's general guidelines for High Risk Data.
Definitions
De-identification
De-identification is the removal or alteration of information in a dataset in order to make it more difficult or impossible to identify specific individuals. Data which has been HIPAA de-identified has had all HIPAA identifiers removed. What constitutes “anonymized” data may vary across different data protection laws. View Stanford's Data De-identification Overview and Guidance for more details on GDPR "anonymous" and "pseudonymous" data.
Minimum Privacy Standards (MinPriv)
The Minimum Privacy Standards are intended to reflect best practices for the collection, processing, transfer, deletion and other use of personal data at Stanford.
Minimum Security Standards (MinSec)
The Minimum Security Standards are intended to reflect the minimum level of care necessary for Stanford's sensitive data.
Personal Data
Any information that relates to an identifiable, unique human being.
Protected Health Information (PHI)
All individually identifiable health information that relates to a patient's past, present, or future physical or mental health or condition, the provision of health care to a patient, or the past, present, or future payment for health care provided to a patient. For questions about whether information is considered to be PHI, contact the University Privacy Office. View 18 HIPAA identifiers of PHI.
Sensitive Data
Any information that must be protected against unauthorized disclosure; its loss, misuse, modification, or unauthorized access could negatively impact an organization or individual.* At Stanford, sensitive data includes these risk classifications: Moderate Risk, High Risk Non-PHI, and High Risk PHI.
*What constitutes "sensitive personal data" is defined by applicable data protection laws.
Help and training
If you suspect or know of a data compromise or risk, immediately report the incident to keep you and others safe:
![]()
Report a UK Biobank incident
Note: For any incidents involving UK Biobank data, view the UK Biobank reporting protocols here.
Get help
University Privacy Office: Get help related to privacy questions.
University IT Information Security Office: Get help related to IT security.
Stanford Health Care Privacy Office: Get help related to patient data and PHI.
- PrivacyOfficer@stanfordhealthcare.org
- Privacy Office main line: 650-724-2572
- 24/7 Compliance Hotline, including anonymous reporting: 800-216-1784
Research Compliance Office (IRB): Get help related to human subject research and the protection of participants.
Training and resources
University Privacy Office Training
- University Privacy Office Training (HIPAA, FERPA, GDPR, Privacy Office Tutorials)
University IT Information Security Office Resources
Stanford Medicine Training and Resources
Make your commitment
Once you complete this form*, you will automatically receive an email with the details of your commitment. You can also choose to send your commitment to individuals you choose.
*Note this commitment does not act as a replacement for the official training. This web page is a supplemental resource.
