Stanford Bug Bounty Program
After careful consideration, the Stanford Bug Bounty Program will no longer offer bounty rewards for submissions, effective immediately and until further notice.
We deeply appreciate the community’s engagement and contributions over the years, which have significantly strengthened our systems. Your dedication has been invaluable.
Moving forward, all new vulnerability submissions will be processed through Stanford University’s Vulnerability Disclosure Program (VDP). Please visit vdp.stanford.edu for details on how to submit vulnerabilities under this program.
Thank you for your continued support and understanding.
Stanford Information Security Team
The Stanford Bug Bounty program is an experiment in improving the university’s cybersecurity posture through formalized community involvement. Subject to the terms below, the Information Security Office is offering rewards for the responsible discovery and disclosure of system vulnerabilities.
Scope
Scope
Only the following domains are in-scope:
- bi.stanford.edu
- accessories.stanford.edu
- Active Directory
- win.stanford.edu
- Cardinal Print
- cardinalprintcenter.stanford.edu
- printer interface
- *.sahr.stanford.edu
- ecm.stanford.edu
- fasa.stanford.edu
- secureportal.stanford.edu
- regadmin.stanford.edu
- ice.stanford.edu
- iron.stanford.edu
- campusmap.stanford.edu
- code.stanford.edu
- accounts.stanford.edu
- authority.stanford.edu
- idp.stanford.edu
- login.stanford.edu
- mydevices.stanford.edu
- spdb.stanford.edu
- sponsorship.stanford.edu
- stanfordwho.stanford.edu
- stanfordyou.stanford.edu
- vault.stanford.edu (new)
- who.stanford.edu
- workgroup.stanford.edu
- Kerberos authentication
- Stanford VPN
- Stanford LDAP
- Stanford Network Access Control (SUNAC)
- netdb.stanford.edu
- mailman.stanford.edu
- gsb.stanford.edu(new)
- gsbapexuat2.stanford.edu(new)
- GSBgo(Mobile App)
- stanfordmag.org
- covidsupport.stanford.edu
- covidstudentsupport.stanford.edu
- Card Services sites
Examples of in-scope vulnerabilities:
- Remote Code Execution (RCE)
- SQL injection
- XML External Entity Injection (XXE)
- Authorization bypass/escalation
- Sensitive information leaks
- Cross-site scripting (XSS)
- Cross-site request forgery (CSRF)

Out-of-scope vulnerabilities:
- Any bug that does not pose a substantial or demonstrable security risk
- Clickjacking, open redirects, or lack of security headers
- Denial of service (DOS)
- Social engineering
- Physical exploits of our servers or network
- Local network-based exploits such as DNS poisoning or ARP spoofing
Rules

Rules
- In order to take part in this program, you must be a Stanford student (undergraduate/graduate), postdoc, or full-time benefits eligible employee.
- For employees, participation in the bug bounty program must not interfere with job responsibilities and should be conducted outside of work hours.
- Any involvement you have with an in-scope domain that could create a conflict of interest renders that domain out-of-scope for you.
- Do not publicly disclose any vulnerabilities without explicit written permission from the Information Security Office at Stanford University.
- Do not perform any tests that will disrupt services or impair others' ability to use them.
- Do not use automated scanners.
- To be eligible for bounty, all testing must be performed within the scope described above. Out-of-scope submissions will be accepted and acted upon, but are not eligible for bounty.
- If you become aware of a vulnerability involving an out-of-scope domain, it is still appropriate to report the vulnerability via this program, and the same safe harbor provisions apply to protect those who responsibly report.
- Access does not equate to authorization. If a vulnerability provides unintended access to data, do not access the data beyond the minimum extent necessary to effectively demonstrate the presence of a vulnerability. If you encounter any Moderate or High Risk data during testing (such as Personally Identifiable Information (PII), Protected Health Information (PHI), credit card data, or other confidential information), cease testing and submit a report immediately.
- Testing must not violate the Stanford Honor Code, Fundamental Standard, Admin Guide Chapter 6.2.1, or any applicable laws.
- To the furthest extent possible, only interact with test accounts you own or accounts with explicit permission from the account owner.
Rewards

Rewards
Stanford reserves the right to not reward any submission if we so choose, and we will not provide compensation for time spent researching.
Bounties are awarded only to the first unique report of a previously unidentified vulnerability. Subsequent reports will be closed as duplicates and not eligible for a bounty.
Vulnerability severities and reward amounts are determined at the discretion of the Information Security Office. For instance, a cross-site scripting vulnerability on a static, unauthenticated website may be classified as less severe compared to a cross-site scripting vulnerability that has the potential to compromise user accounts.
Cumulative rewards in excess of $50 are taxable, and you must report it as income on your tax returns.
Reward amounts and vulnerability severity classifications are subject to change at any time.
Severity | Reward Amount (in USD)
Severity Reward Amount (in USD) Critical $500-$1,000 High $100-$800 Medium $50-$100 Low $50 Accepted Risk or Informational $0
Vulnerability | Severity Range | Points
Vulnerability Severity Range Points Remote Code Execution Critical 500 SQL Injection High - Critical 500 XXE High - Critical 500 XSS Medium - Critical 300 Server-Side Request Forgery Low - Critical 300 Directory Traversal - Local File Inclusion Medium - High 300 Authentication/Authorization Bypass (Broken Access Control) Medium - High 300 Privilege Escalation Medium - High 300 Insecure Direct Object Reference Medium - Critical 300 Misconfiguration Low - High 200 Web Cache Deception Low - Medium 100 CORS Misconfiguration Low - Medium 100 CRLF Injection Low - Medium 100 Cross Site Request Forgery Low - Medium 100 Open Redirect Low - Medium 50 Information Disclosure Low - Medium 50 Request smuggling Low - Medium 50
Bonus Points
In addition to being eligible for the Bug Hunter Wizard tier of badges, reports that are received with a clear impact statement and detailed remediation recommendations will receive 100 bonus points for their submissions.
Risk Class
Reports on systems classified as High Risk will receive the highest bounty for the vulnerabilities’ severity range.
Safe Harbor
Safe Harbor
When conducting vulnerability research within the terms of this program, we consider such research to be:
- Authorized in accordance with the Computer Fraud and Abuse Act (CFAA) (and/or similar state laws), and we will not initiate legal or disciplinary action against you;
- Exempt from the Digital Millennium Copyright Act (DMCA), and we will not bring a claim against you for circumvention of technology controls;
- Exempt from restrictions in the Stanford Administrative Guide 6.2.1 that would otherwise prohibit conducting such security research, and we waive those restrictions on a limited basis for research performed pursuant to this program; and
- Lawful, helpful to Stanford's cybersecurity posture, and conducted in good faith.
You are expected, as always, to comply with all applicable laws. Any unauthorized activity outside the terms of this program will be subject to disciplinary and/or legal action pursuant to applicable laws and Stanford policies.
If at any time you have concerns or are uncertain whether your security research is consistent with the terms of this program, please submit your question via the vulnerability submission form.
Get Started
Get Started
Out-of-scope submissions will be accepted and acted upon, but are not eligible for bounty. If you become aware of a vulnerability involving an out-of-scope domain, it is still appropriate to report the vulnerability via this program, and the same safe harbor provisions apply to protect those who responsibly report.
Timeline
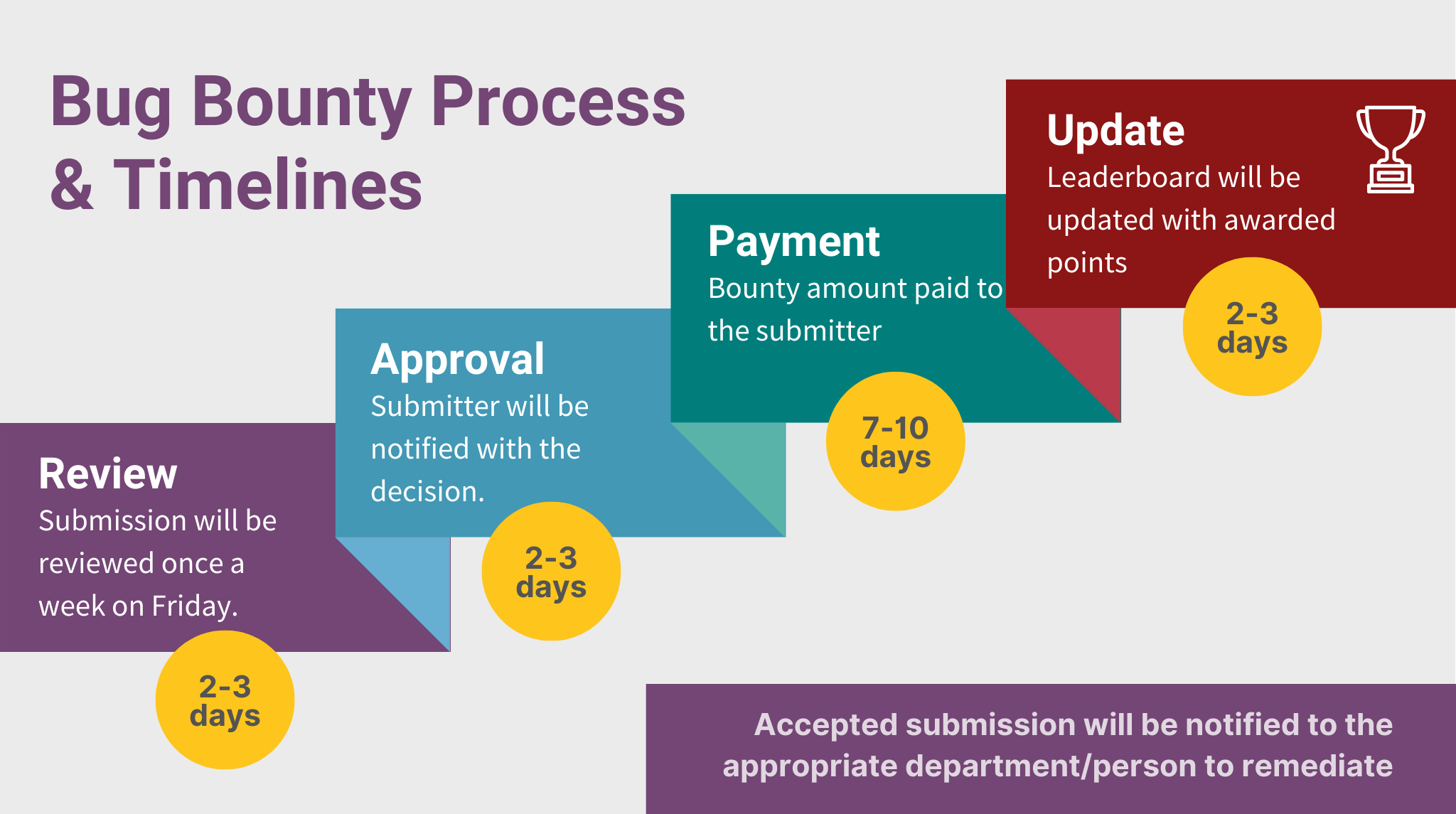
Timeline for Submissions
- Reports received will be reviewed once a week on Fridays
- Once the report is accepted a ticket is created to pay the security researcher and will be processed by the following Friday
- The leaderboard will be updated on the day the submission is triaged and accepted
Bug Bounty Stats
109 submissions
$13,835 total rewards
Leaderboard
Last updated May 2024
| Username | Reputation Points | Number of Submissions |
|---|---|---|
hawklin | 450 | 2 |
mccain | 400 | 1 |
saligrama | 400 | 1 |
zstjohn | 400 | 1 |
mavlevin | 300 | 1 |
akshay01 | 300 | 1 |
ghusman | 100 | 1 |
rlama22 | 50 | 1 |
brianamb | 50 | 1 |
sheamck | 50 | 1 |
Badges and What They Mean
Cardinal Tree Tier Description 
Cardinal Tree Tier 1
This icon is given to security researchers on their first submission 
Cardinal Tree Tier 2
Awarded to security researchers who submit 5+ reports 
Cardinal Tree Tier 3
Awarded to security researchers who submit 10+ reports Bug Hunter Wizard Tier Description 
Bug Wizard Tier 1
Awarded to security researchers who submit 20+ reports and provide clear impact statements with detailed remediation recommendations 
Bug Wizard Tier 2
Awarded to security researchers who submit 30+ reports and provide clear impact statements with detailed remediation recommendations 
Bug Wizard Tier 3
Awarded to security researchers who submit 40+ reports and provide clear impact statements with detailed remediation recommendations

