Data Sanitization
On this page:
Data sanitization is the process of irreversibly removing or destroying data stored on a memory device (hard drives, flash memory / SSDs, mobile devices, CDs, and DVDs, etc.) or in hard copy form. It is important to use the proper technique to ensure that all data is purged. Our guidance below is derived from NIST SP 800-88 Rev. 2 (PDF): Guidelines for Media Sanitization.
Policy
The policies below define baseline controls for the sanitization and disposal of university data:
Device Transfer Within Stanford
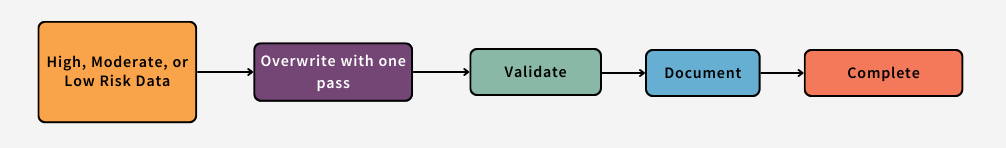
All Low, Moderate, High Risk Data stored on the device must be sanitized when a device is transferred between organizations. Please follow the Data Sanitization Guidelines below.
Device Disposal or Device Transfer Off-Campus
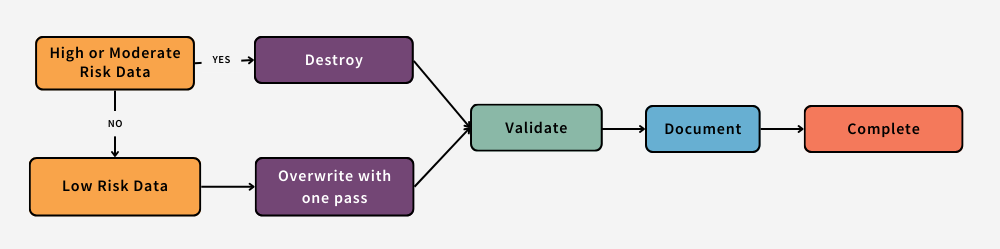
If a device is to be disposed of or transferred to a party outside of the University, the device owner or local property administrator must sanitize or remove and physically destroy all device storage regardless if the device is known to contain any High, Moderate, or Low Risk Data. Local property administrators should be prepared to either sanitize or destroy the disk themselves according to the Data Sanitization Guidelines below (and keep a record of the activity) or contact the Information Security Office for assistance.
Personally Owned Devices Leaving the University
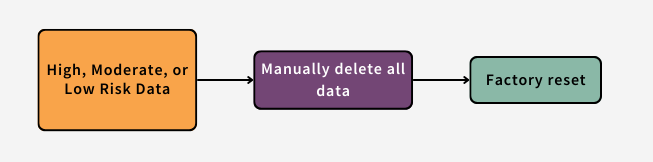
All High, Moderate, or Low Risk Data stored on the device must be sanitized according to the Data Sanitization Guidelines below.
Data Sanitization Guidelines
Mobile Devices
| iOS: Apple iPhone and iPad |
|
| Android OS |
|
| Windows Phone OSA7.1/8/8.x |
|
| Other devices |
|
Individual File*
* See Flash Memory section below for special requirements pertaining to solid state memory / SSD.
| Mac OS X |
|
| Windows | |
| Linux |
|
Flash Memory
Flash memory-based storage devices, or Solid State Drives (SSDs), have become prevalent due to falling costs, higher performance, and shock resistance. Because flash memory operates fundamentally differently from magnetic media, overwriting does not necessarily clear all of the data. For the proper sanitization of flash memory, invoking special data purge commands built into the SSD hardware is the best approach.
| ATA Solid State Drives (SSDs) (including PATA, SATA, eSATA, and SCSI) |
AND
and/or
|
| USB Removable Media and Memory Cards |
and/or
|
Magnetic Media
| Magnetic disks (including floppy disks, ATA and SCSI hard disk drives) |
and/or
and/or
and/or
|
Optical Media
| CD, DVD, Blu-ray Disc |
and/or
|
Hard Copy Storage
| Paper |
or
|
For guidance on other media not listed above, please refer to NIST SP 800-88 Rev. 1 ("Guidelines for Media Sanitization") and the manufacturer manuals for appropriate data sanitation techniques, commands, and tools.
Validate
The validation step in the data sanitization process involves testing the device/media to ensure the information cannot be read.
Document
During the data sanitization process, be sure to document the following information for your own records.
- Manufacturer
- Model
- Serial Number
- Property Number
- Media Type
- Media Source
- Pre-sanitization confidentiality categorization
- Sanitization description
- Method used
- Tool used
- Verification
- Method
- Post-sanitization destination
- Name of Person, Date, Location, Contact Information, Signature
