Qualys - Frequently Asked Questions
Program and Governance
- What is the general overview of the vulnerability management program?
-
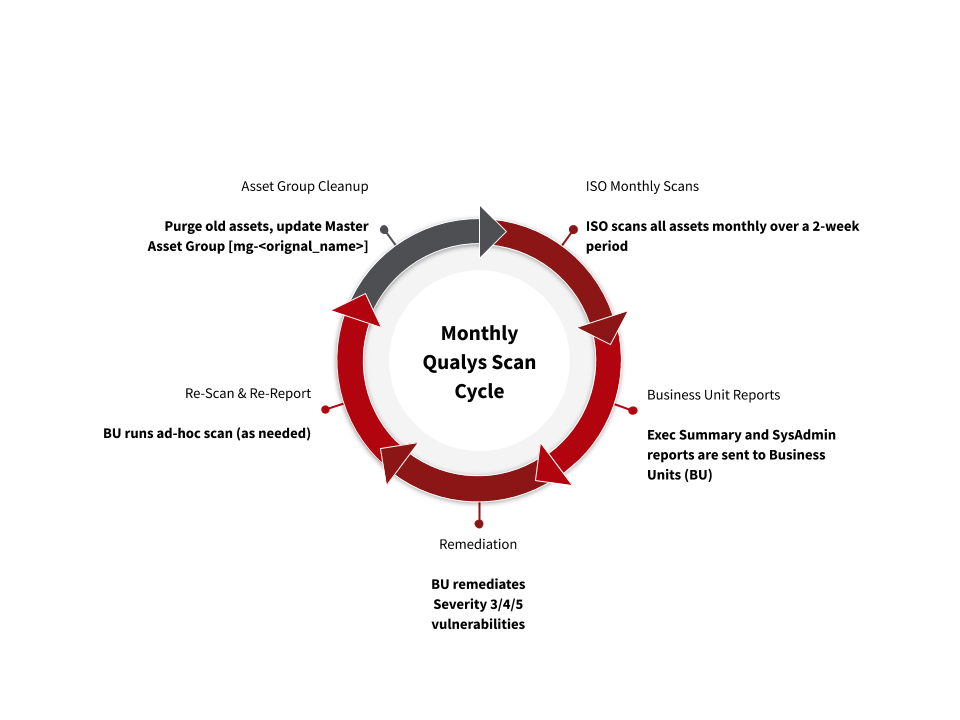
ISO, working in conjunction with IT staff in the various university organizations, follows these steps to identify, assess and remediate vulnerabilities.
- ISO scans all Stanford assets (anything responding to a Stanford assigned IP address) at least once each month.
- At the beginning of each month, ISO sends reports that contain information about the confirmed level 3, 4 and 5 vulnerabilities that need to be remediated.
- The reports are sent via email to the Stanford departments, known as "business units" in Qualys.
- Business units receive vulnerability information for the IP addresses they have identified responsibility for. This is done through the creation of an asset group called a "master asset group".
- Business units are responsible for ensuring that they have at least one master asset group and that it is fully reflective of their scope of responsibility.
- Business units are to review the ISO provided reports and remediate severity 3/4/5 vulnerabilities within the time period specified by the Minimum Security Standards.
- Using Qualys, the business unit may create reports above and beyond what ISO provides, as necessary, to meet internal operational needs.
- After remediation, business units are free to run ad-hoc scans against assets using the appropriate scanner appliance (the scanner in the same operational area where the asset resides).
- How often does the Qualys Governance group meet and what is discussed?
- The Qualys Governance group meets at leats once monthly and decides strategic direction for the program, reviews requests for global QID exclusions, and makes decisions on modification of risk levels of QIDs.
- Where can I view the outcomes of the most recent governance meetings?
- The Qualys Governance maintains a web page where outcomes of governance meetings are captured and made available to the community.
The page can be found at: https://uit.stanford.edu/service/qualys/governance - What is the process for dealing with large scale false positives?
-
If there is a false positive vulnerability across several/all systems, submit a Help ticket and ISO will review the vulnerability QID in the next Qualys Governance meeting.
If the false positive vulnerability exists on only a few systems, see How To Ignore A Vulnerability (individual or in bulk) and Report on Ignored Vulnerabilities.
ISO periodically runs a report on ignored vulnerabilities across all assets to ensure that no legitimate vulnerabilities (such as weak ciphers) are ignored.
- What is the criteria ISO has established in which a QID severity may be reclassed?
-
ISO may reclassify a vulnerability (i.e. moving it from a severity 3 to a severity 2) only when the following criteria have been met:
- The QID is considered to be information disclosure, and
- The remediation action suggested by Qualys is only that of network segmentation.
- What is the criteria ISO has established in which a QID may be globally ignored?
- ISO may choose to add a QID to the "ISO Managed Excluded QIDs" list only after the Qualys Governance group has come to an agreement that the risk level is low and that the QID is commonly a false positive. The QID is only ignored in the ISO provided monthly reports, but will remain on the asset itself.
Business units and asset groups
- What are master asset groups? Who is responsible for creating and maintaining master asset groups?
-
Master asset groups are asset groups created by each business unit in Qualys that contain the business unit’s network IP address range.
ISO creates vulnerability reports based on these master groups and sends the reports to the respective business unit.
Business units are responsible for properly maintaining master asset groups, by updating and purging old assets and asset groups.
- How many master asset groups should each organization have?
- Each business unit should have at least one Master Asset Group, but can have as many master asset groups as they want. ISO recommends that business units maintain the minimum number of master asset groups that provide the most accurate information with non-overlapping assets.
- How do I configure the Master Asset Group in Qualys?
-
- Log in to Qualys using your SUNet ID and password.
If you have not used Qualys before, submit a Help ticket to request an account. - Navigate to the Asset Groups tab under Vulnerability Management in Qualys (Assets -> Asset Group).
- Use Search or Filters to navigate to your asset groups.
- Consolidate your assets into a single, or as few as possible, Master Asset Groups. Name or rename the asset group “mg-”<MyAssetGroup>. The prefix “mg-” is important as it will be used by an ISO script to generate sub-groups.
- Log in to Qualys using your SUNet ID and password.
- Who is responsible for purging assets and is there any policy about that?
- When a business unit retires an asset, they should purge that asset from Qualys. Only unit managers have the capability in Qualys to purge assets. ISO periodically removes assets when they do not appear on a scan for more than 90 days.
- I can’t view scanners to scan my asset group? What do I do?
- Work with your business unit’s unit manager to add the scanner group to your account.
Scanning
- What is the ISO default option profile used for scanning in normal situations?
- ISO default option profile: ISO Official 3/4/5 (Site-wide) (default)
- What is the ISO default option profile used for scanning sensitive devices?
- ISO option profile for special scans: ISO 3/4/5 (special vsys Lower Intensity)
- I don’t have access to all scanners - How do I get access?
- Please reach out to your business unit’s unit manager to grant you access to the scanners. You can also submit a Help ticket.
- I think Qualys scans are causing service interruptions. What should I do?
- Please submit a Help ticket. ISO will set up test scans on your systems to validate that it is Qualys that is disrupting your services. If it is, then ISO will set up the lowest intensity scans on your systems. If the lowest intensity does not resolve the issue, the systems will be added to an “Exclude from Scan” list.
Reporting
- What type of reports does ISO send and when?
- ISO sends two types of reports on 1st of every month:
- Executive report: A one page report that summarizes the number of confirmed 3/4/5 vulnerabilities and the number of systems affected.
- Sys-Admin report: A detailed vulnerability report including severity level, threat, impact and solution for each vulnerability.
- What are the templates used for system administrator reports and executive reports?
-
- Executive report: ISO Monthly Scan Executive XML - Confirmed 3/4/5
- Sys-Admin report: ISO Monthly Scan SysAdmin - Confirmed 3/4/5
The above templates are globally available and can be used by all Qualys users to generate reports.
- What are the report templates that I can use for generating custom reports?
- You can use the globally available templates or create your own template to generate reports.
- What are the steps to generate reports in Qualys?
-
- Log in to Qualys using your SUNet ID and password.
- Navigate to Vulnerability Management > Reports > Templates.
- Hover over the scan report template that you want to run.
- From the Quick Action menu, select Run.
- What is the format of reports sent to system administrators and executives?
- The system administrators’ reports are sent in PDF format and the executive reports are sent as email body text.
- What vulnerabilities are excluded by ISO in the scan reports?
- The following vulnerabilities are identified as common false positives and are currently excluded from the reports:
- 105459: EOL/Obsolete Software: SNMP Protocol Version Detected
- 68521:NFS-Utils Xlog Remote Buffer Overrun Vulnerability
- 66040: Statd Format Bug Vulnerability
