Best Practices: Configuring your EC2 or SES service for sending email
The “What”
An email service provider has blocked messages originating from my AWS EC2 or SES service.
The “Why”
Each vendor has the right to protect their services and other customers from malicious actors. This may occur when another customer on the same backend cloud infrastructure has misconfigured a service or has decided to use that cloud infrastructure to send malicious messages. Services like Google, Microsoft, and ProofPoint (Stanford’s vendor for email security) as well as Internet Service Providers have the right to act in the best interest of their customers and their business. To protect their customers, email service providers and Internet Service Providers may block messages originating from large network ranges when issues like these are discovered.
Please note the directions below are specific to AWS’ SES and EC2 servies. Functionality similar to AWS EC2 instances also exist within the Azure and GCP platforms. The steps would be similar for messages originating from one of those other platforms, but the required forms to make requests to those vendors would be different.
Also note, the instructions below greatly improve message reliability; however, email service providers and internet service providers may still block your IPs if they deem messages from those addresses to be malicious, spam, or otherwise unwanted.
Recommended best practices for configuring outbound email on AWS services, EC2 and SES.
Suggestion to reduce the chance of an IP(s) being added to a blocklist by email service providers for AWS EC2 instance:
- Reserve an EIP for the EC2 instance.
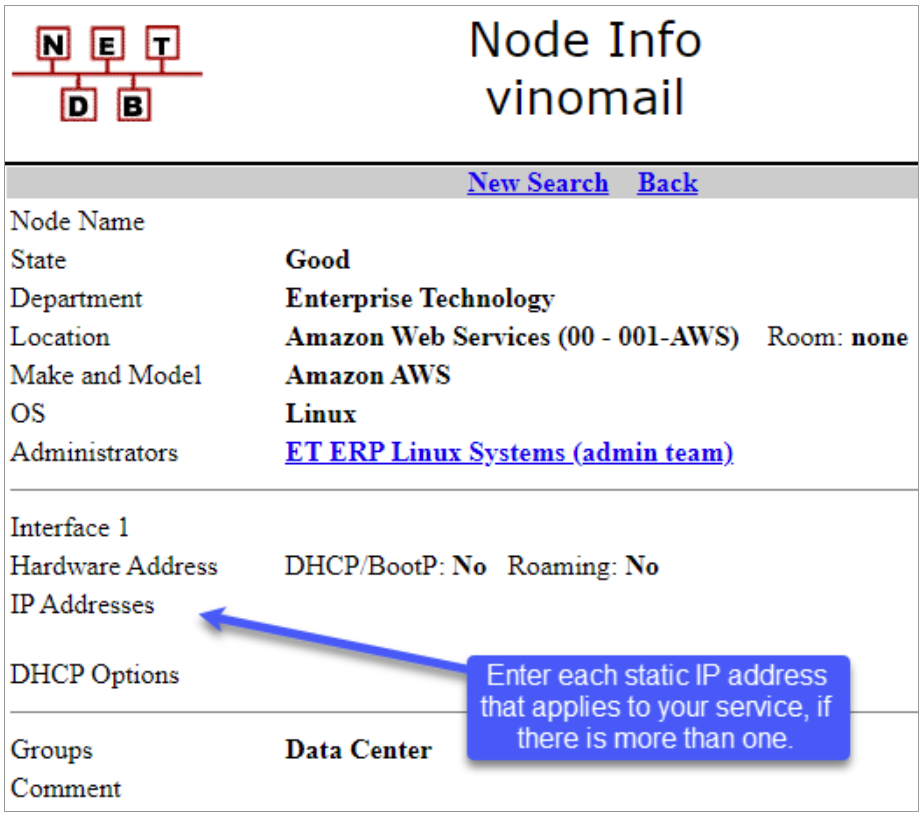
- Create a node in Netdb with the EIP.
- Provide AWS with your Reverse DNS records using this form. (https://console.aws.amazon.com/support/contacts?#/rdns-limits) so they can create the mappings.
Suggestion to reduce the chance of an IP(s) being added to a blocklist by email service provider for AWS SES:
- Request dedicated IP(s) for AWS SES.
- Create a node in Netdb with the dedicated IP.
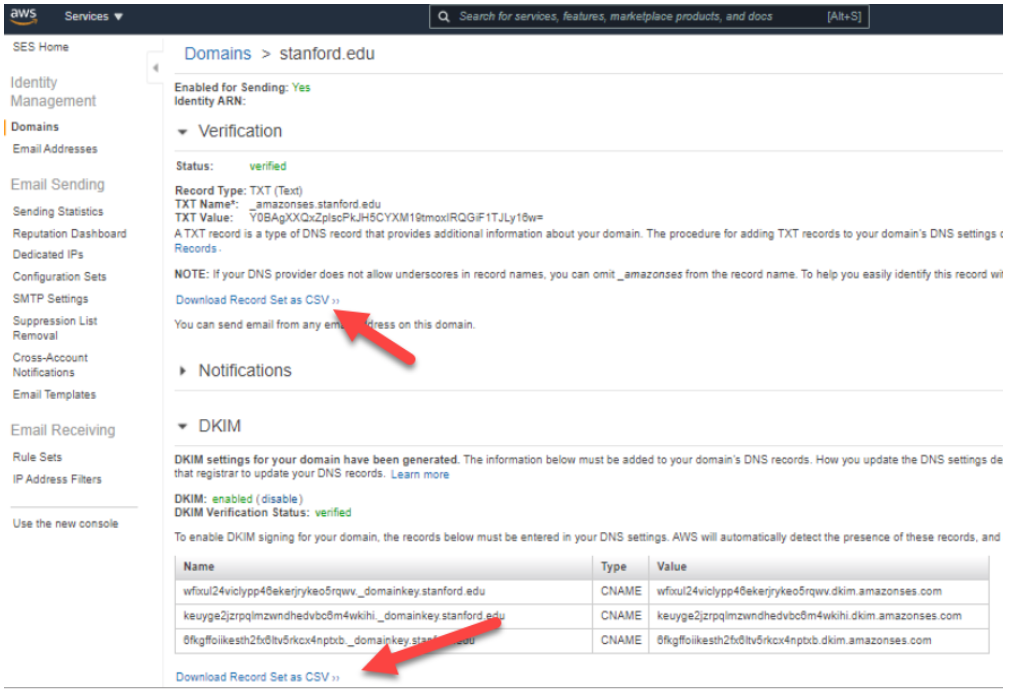
- Since AWS SES doesn't support rDNS, we can enable DKIM signing for the sender domain(s).
- Provide the TXT record with the displayed Name and Value and the three CNAME (these record sets can be downloaded from SES Home -> Domains, see screenshot below) to the Stanford networking team to publish TXT records to DNS for domain verification and DKIM signing purpose in DNS.
- Sample text for SNOW ticket
AWS EC2 / AWS SES - hosted on AWS to send bulk emails to Stanford's recipients. We need assistance in publishing TXT records to DNS for domain verification and DKIM signing purposes.
NOTE: If a POC instance please include an expiration date for the DNS record. If this is for a production system please indicate that there is no expiration date.
- Example TXT record
Download both CSV files and attach them to the Service NOW request.
- Example NetDB Record: 54.240.84.151