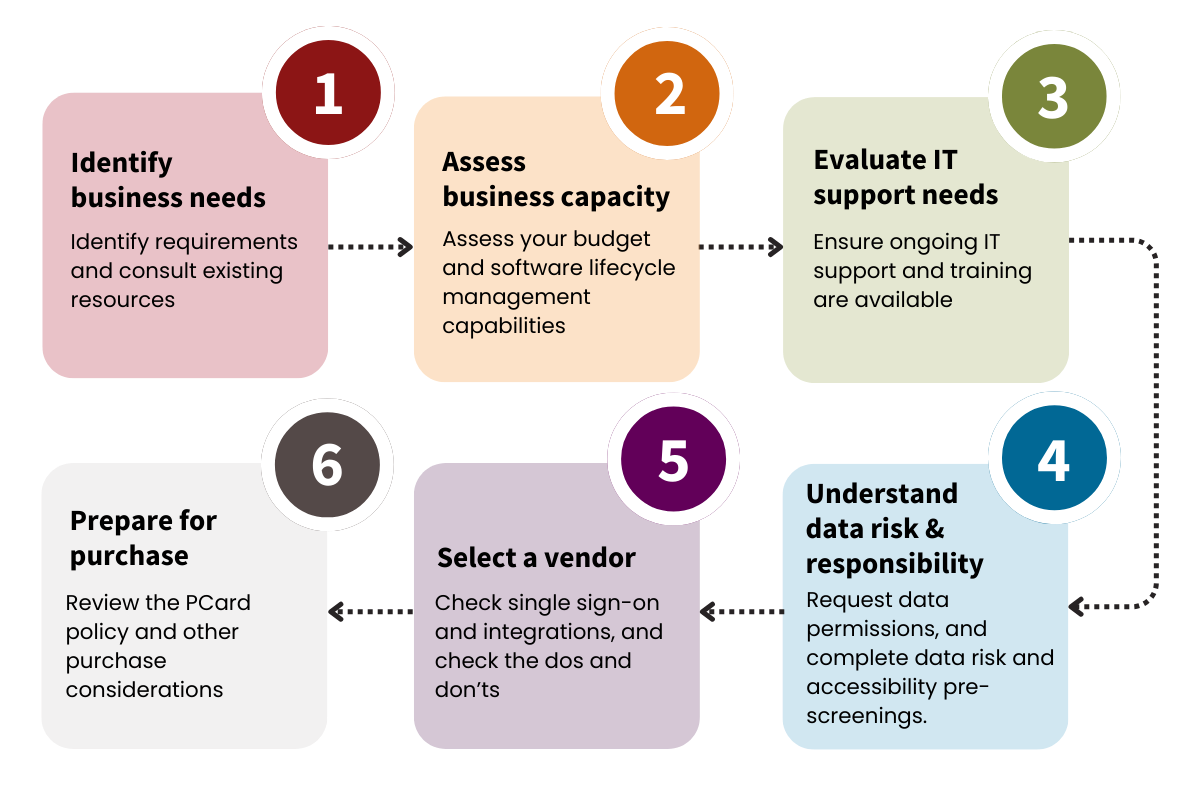
Key requirements
Compile a list of essential features the software must possess to meet your business objectives.
Consider whether other departments have similar needs or existing solutions. Collaboration can lead to unified software purchases. Leverage the Campus IT Plan to find out.
Consult existing resources
Before purchasing new software outside of Stanford providers, search the Software at Stanford catalog to see if it is already provided.
For additional support, engage with UIT Business Relationship Managers, Software Licensing, or local IT support for insights into software already available or might become available soon.
Search Software at Stanford