Registry Integration x509 Certificates How-to
- How do I request a new certificate?
-
- Identify what service you need (person/student/account/course/authority/workgroup).
- Generate a new key and CSR (see question below).
- Submit the CSR via Certificate Manager at https://registrycm.stanford.edu.
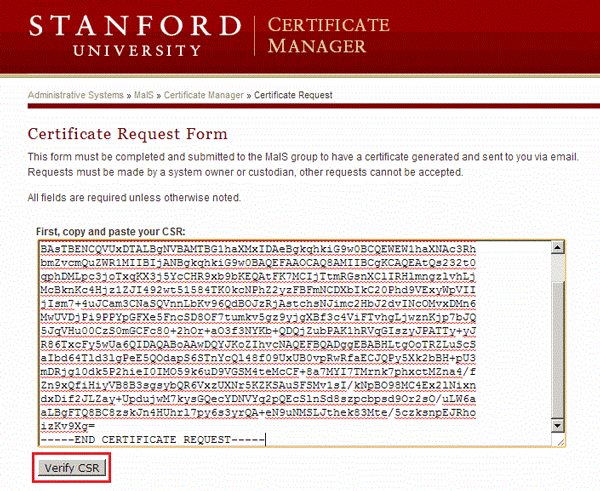
-
Once your certificate request is approved, download the file.
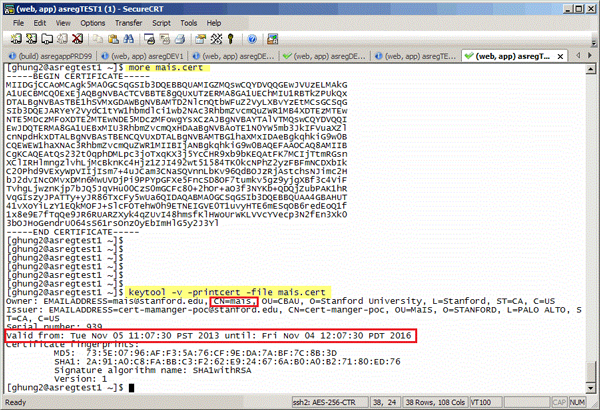
- Construct the keystore/.p12 file as needed (see question below).
- How do I generate a CSR and a private key?
-
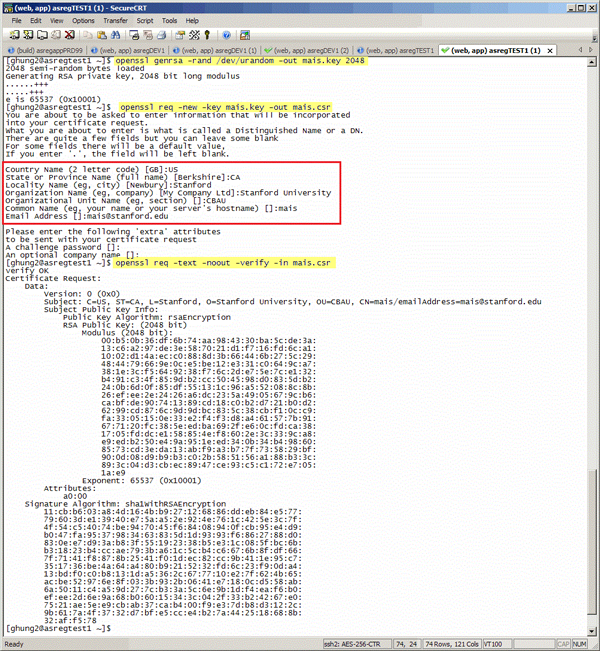
- To generate a private key file, run the following commands:
$ openssl genrsa -rand /dev/urandom -out [key file] 2048
example: openssl genrsa -rand /dev/urandom -out mais.key 2048- To generate a certificate signing request (CSR) from the private key:
- Prepare to provide the following information:
- Country Name (2 letter code) [GB]:US
- State or Province Name (full name) [Berkshire]:CA
- Locality Name (e.g., city) [Newbury]:Stanford
- Organization Name (e.g., company) [My Company Ltd]:Stanford University
- Organizational Unit Name (e.g., section) []:your 4-digit org code
- Common Name (e.g., your name or your server's hostname) []:mais-app
- Email Address []:mais@stanford.edu
*Note: Common name should be constructed in this fashion: [org/project]-[application], such as mais-havester
- Once you have prepared the above information, run the following commands:
$ openssl req -new -key [key file] -out [csr file]
example: openssl req -new -key mais.key -out mais.csr - To verify the CSR, run:
$ openssl req -text -noout -verify -in [csr file]
example: openssl req -text -noout -verify -in mais.csr
- I downloaded the signed certificate, how do I construct a .p12/keystore file?
-
- Use OpenSSL to construct the file (you will need to create a password with this step):
$ openssl pkcs12 -export -name [alias name] -in [certificate file] -inkey [key file] -out [p12 file]
example: openssl pkcs12 -export -name [mais] -in mais.cert -inkey mais.key -out mais.p12 - Import the CA cert into a keystore:
$ keytool -alias registryca -importcert -file cacert.cer -keystore [keystore file]
example: keytool -alias registryca -importcert -file cacert.cer -keystore mais.jks - Import the .p12 file into a keystore:
$ keytool -v -importkeystore -srckeystore [p12 file] -srcstoretype PKCS12 -destkeystore [keystore file] -deststoretype JKS
example: keytool -v -importkeystore -srckeystore mais.p12 -srcstoretype PKCS12 -destkeystore mais.jks -deststoretype JKS - View the keystore:
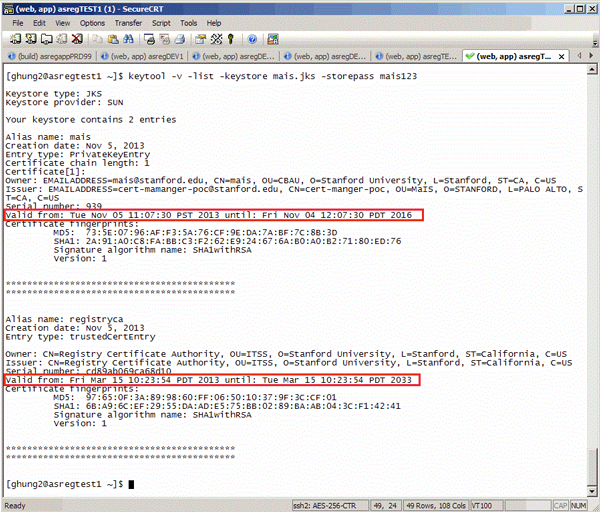
$ keytool -v -list -keystore [keystore file] -storepass [keystore password]
example: keytool -v -list -keystore mais.jks -storepass [mais password]
- Use OpenSSL to construct the file (you will need to create a password with this step):
- My certificate isn't working. What should I do?
-
Verify that your certificate has not expired:
- Use Keytool to check keystore/jks files
$ keytool -v -list -keystore [keystore file] -storepass [keystore password] example: keytool -v -list -keystore mais.jks -storepass [keystore password]
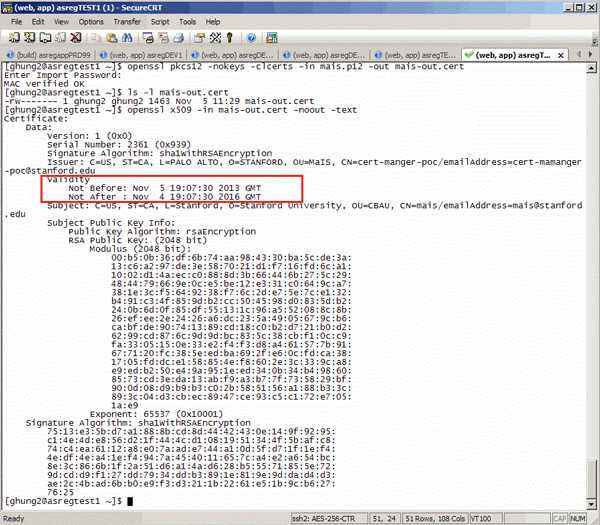
- Use OpenSSL to check p12 files by exporting the certificate file first, then view
$ openssl pkcs12 -nokeys -clcerts -in [p12 file] -out [certificate file]
example: openssl pkcs12 -nokeys -clcerts -in mais.p12 -out mais.cert$ openssl x509 -in [certificate file] -noout -text
example:$ openssl x509 -in mais.cert -noout -text
- If the certificate is revoked, contact the MaIS team.
- My certificate is expired. What should I do?
-
- Contact the MaIS team to renew your certificate.
- Download the certificate when renewed.
- Replace certificate in keystore/p12 (see question below).
- My certificate has been revoked. What should I do?
-
- Contact the MaIS team to renew your certificate.
- Download the certificate when renewed.
- Replace certificate in keystore/p12 (see question below).
- How do I replace an existing certificate?
-
- For keystore files, you will need to import the new certificate with the matching CN into the keystore:
$ keytool -import -alias [alias name] -file [new cert file] -keystore [keystore file]
example: keytool -import -alias [mais] -file mais.cert -keystore mais.jks- For p12 files, recreate the .p12 file following these steps:
- Back up your old .p12, key, certificate files if needed.
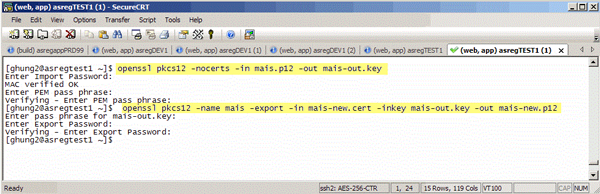
- Extract the private-key from your existing .p12 file (if you don't already have a copy):
$ openssl pkcs12 -nocerts -in [p12 file] -out [key file]
example: openssl pkcs12 -nocerts -in mais.p12 -out mais.key - Recreate the .p12 file with the new certificate plus the extracted private-key from the last command:
$ openssl pkcs12 -name [alias name] -export -in [new cert file] -inkey [key file] -out [p12 file]
example: openssl pkcs12 -name mais -export -in mais.cert -inkey mais.key -out mais.p12
- How do I use the downloaded certificate in a browser?
-
- Create a .p12 file from the certificate (see question above).
- Import the .p12 file into the browser of your choice.
- FireFox
Options > Certificates Tab > View Certificates > Import - Chrome
Settings > Show Advanced Settings > HTTPS/SSL > Manage Certificates > Import - Internet Explorer (IE)
Import or export certificates and private keys - Safari (Mac)
Applications > Utilities > Keychain Access > Login > My Certificates - Safari (Windows)
Safari on Windows uses the certificates installed via Internet Explorer (IE).
- Where do I download the CA Root certificate?
-
The CA Root certificate is available at: https://uit.stanford.edu/sites/default/files/certificates/docservice/registryca.cer
