NetDB Automation for University (Departmental) Firewalls
NetDB Automation for University (Departmental) Firewalls
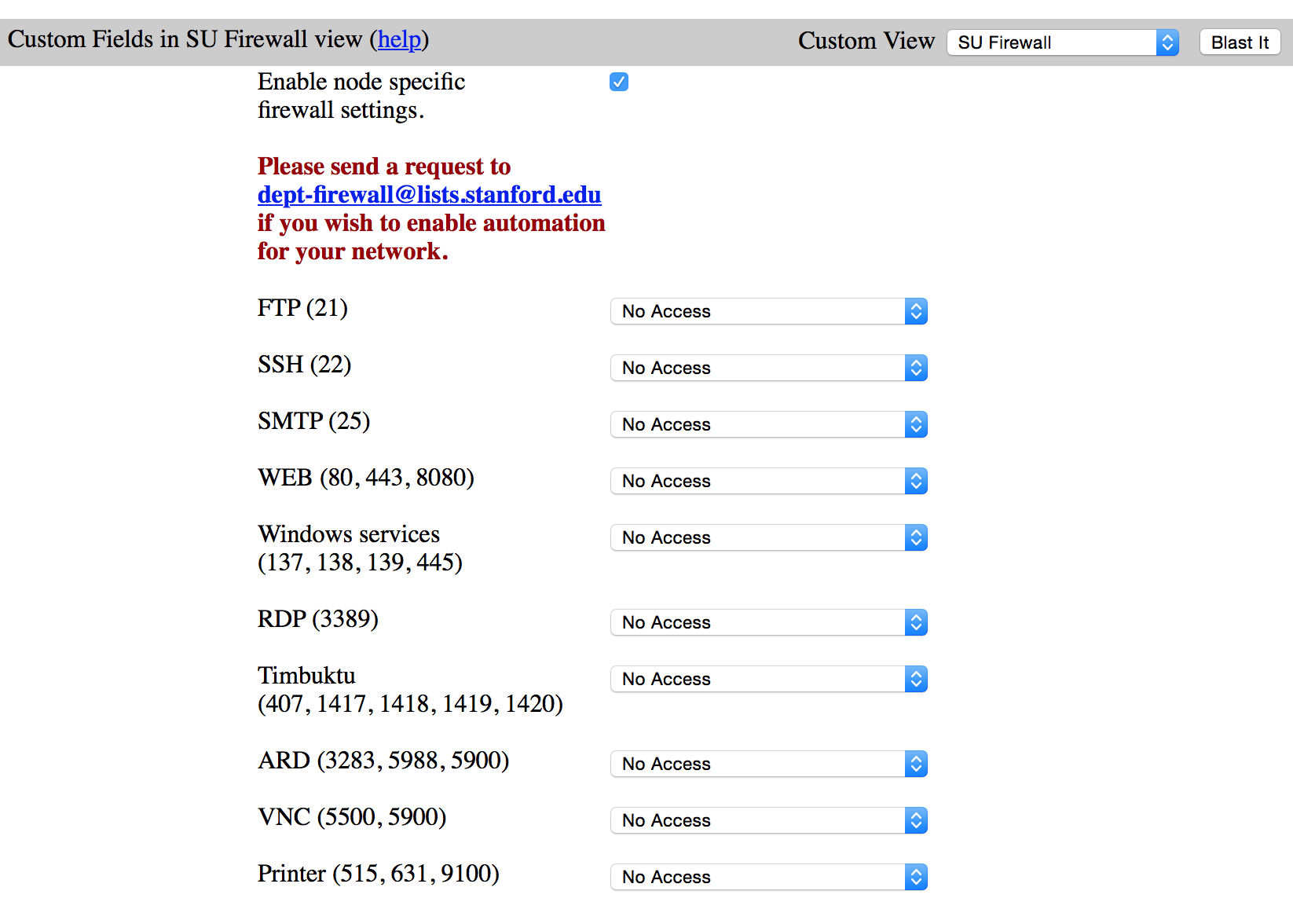
The NetDB automation service provides the administrator of a NetDB node with the option to enable Firewall Policy Template services through the NetDB web interface. Adding a custom field labeled 'SU Firewall' settings allows the administrator to configure access to a set of commonly used services from a number of preset sources.
The purpose of these configuration options is to allow the owner or administrator of a NetDB node record to define rudimentary firewall access to this node without having to submit a regular firewall rule request to the Firewall Team group. The configured settings will have no effect if the network on which the node resides is not secured by a University Firewall.
Sources
Depending on the service and the network one of four sources can be selected which will determine from where the related service can be accessed. Some services will not be accessible from all four sources in accordance with Information Security Office guidelines.
The available source options are:
World Access (w)
- Allow access to the corresponding service from anywhere, campus networks, dorm networks, and any source on the Internet. There are no restrictions in place when accessing this service/port.
Stanford All Networks (s)
- Allow access from all Stanford networks. This covers the administrative, academic and residential networks:
- 10.18.0.0/16, 10.20.0.0/16, 10.30.0.0/15, 10.32.0.0/12, 10.48.0.0/15, 10.96.0.0/11, 10.128.0.0/13, 10.143.0.0/16, 10.200.0.0/16, 10.223.224.0/21, 128.12.0.0/16, 171.64.0.0/14, 172.20.87.128/25, 172.20.128.0/17, 172.20.224.0/21, 172.24.0.0/14, 192.168.15.0/24, 204.63.224.0/21, 2607:F6D0::/32, 2620:6C:40C0::/48
Stanford Admin Networks (a)
- Allow access from the administrative and academic campus networks only:
- 10.18.0.0/16, 10.20.0.0/16, 10.32.0.0/12, 10.48.0.0/15, 10.96.0.0/11, 10.130.0.0/16, 10.131.0.0/16, 10.143.0.0/16, 10.200.0.0/16, 10.223.224.0/21, 171.64.0.0/14, 172.20.87.128/25, 172.20.128.0/17, 172.20.224.0/21, 172.24.0.0/14, 192.168.15.0/24, 204.63.224.0/21, 2607:F6D0::/48, 2620:6C:40C0::/48
Stanford VPN Networks (v)
- Allow access from the public and administrative VPN networks. These networks are a subset of the Stanford administrative networks:
- 10.130.0.0/16, 10.131.0.0/16*
* reserved and included for future expansion
Notes:
- Stanford wireless nets (not including guest wireless) are included in the “Stanford Admin Networks" designation.
- The Stanford wireless network is not firewalled and is not considered part of your local departmental network.
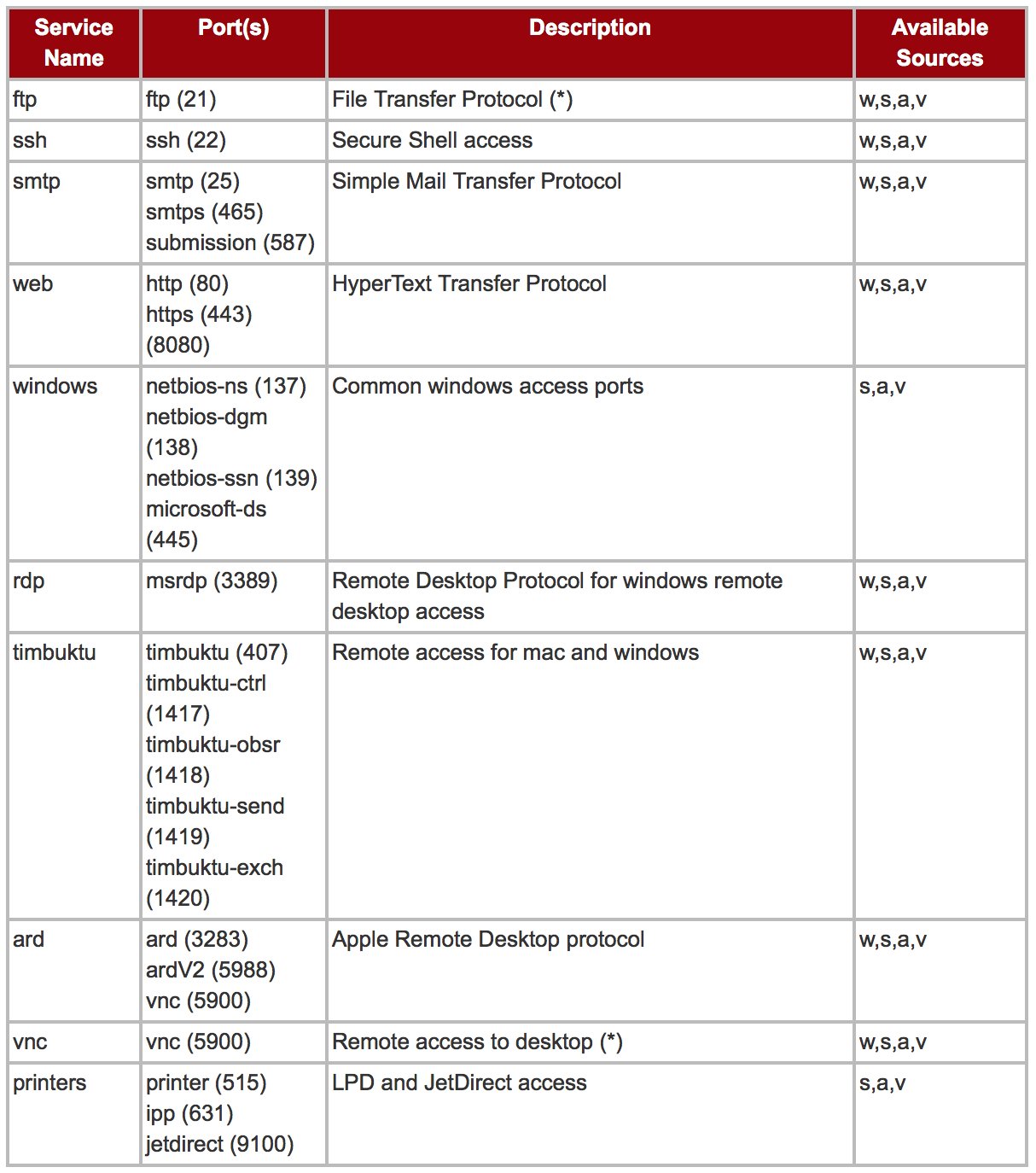
Services
Basic firewall settings for a node can be configured for a limited set of common services, referenced in the table below. Please keep in mind that a service can consist of multiple ports.
Additional Notes:
- Changes to the settings will generally be implemented within 30 minutes once the service is in production.
- Firewall settings will not be implemented unless they have been enabled for the given node. This means that the node will not be configured on the firewall and no settings will be applicable other than the default of the policy for the network on which that node resides. (see example illustration below)