Resources
Merchant Services Program
Merchant Services (MS) is the program that manages, supports, and mitigates risk for payments collected digitally and via credit and debit card at Stanford.
Device Inspection
At each merchant's discretion, a POS owner/department should develop a schedule and routine for device inspection that looks for tampering or substitution periodically.
Approved Service Providers
The Office of the Treasury (OOT) centrally manages Stanford University’s relationship with its acquiring bank to facilitate processing services that meet department needs and adhere to industry and institutional data security standards. This list is constantly being updated.
Internet Service Model and Policy for Independent Third-Party Vendors at Stanford
Stanford third-party vendors must use a separate network for internet service not connected to Stanford.
Vendor Payment Capability Assessment Form
Complete this form before your initial meeting with the merchant services operations team.
New Third-Party Service Provider Evaluation Checklist
Use this checklist to make sure you have enough information to proceed with the new third-party service provider evaluation.
PCI Contractual Language
Refer to the Purchase Order Terms and Conditions Article 18 and 19. Terms in any acceptance by a Seller which are in addition to, or not identical with the following terms will not become a part of any Stanford University Purchase Contract unless Stanford specifically and expressly agrees in writing that such other terms are accepted.
PCI Account Password Change Instructions Self-Service Document
Follow the instructions to change the PCI account created by the PCI Compliance Infrastructure team.
Encrypted Keypad for Virtual Terminal
The SREDKey (secure reading and exchange of data) is an encrypted keypad that ensures all data transactions are protected through secure point to point encryption (P2PE) reducing fraud and data compromise risk.
Third-Party Security Assurance Form by PCI SSC
External Resources by PCI SSC
External websites to help you understand PCI Compliance.
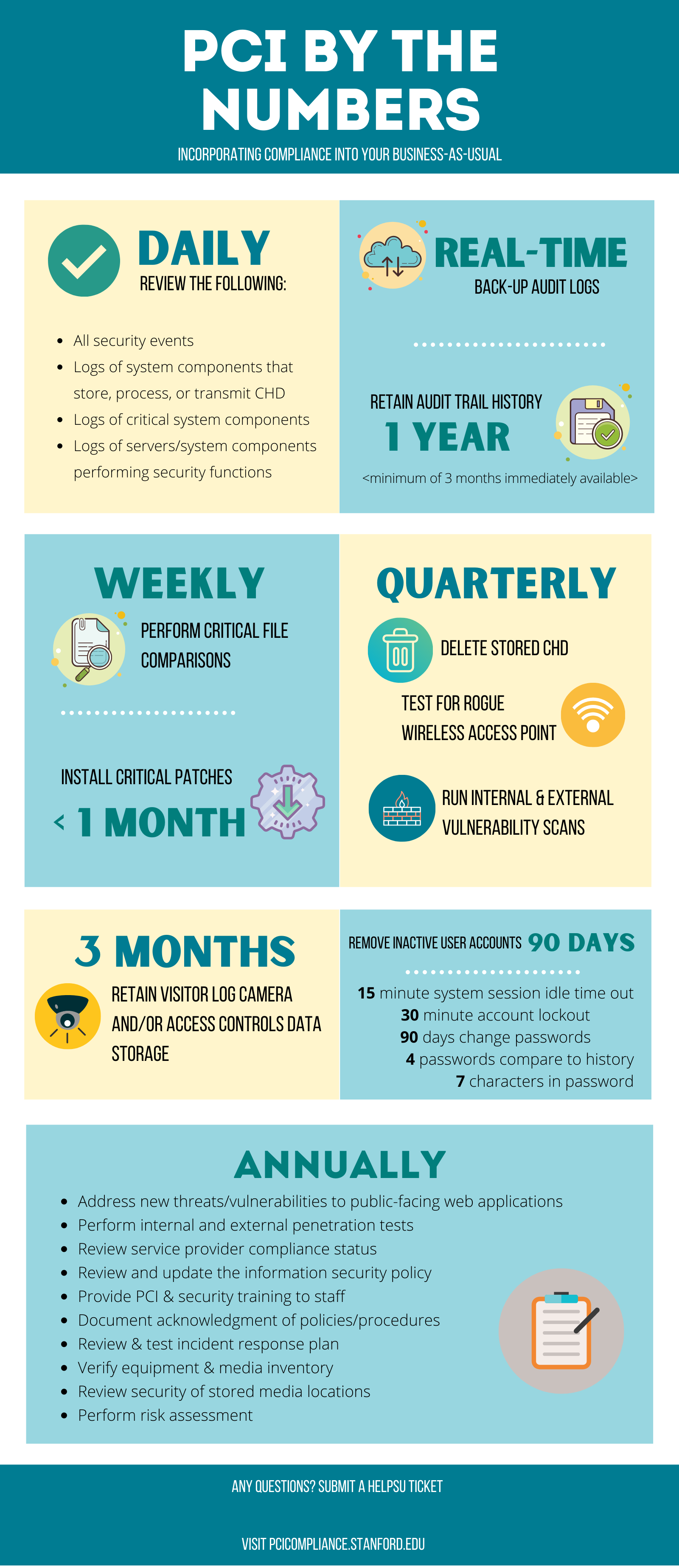
PCI By the Numbers
Incorporating compliance into your business-as-usual
Daily
Review the following:
- All security events
- Logs of system components that store, process, or transmit CHD
- Logs of critical system components
- Logs of servers/system components performing security functions
Real-Time
- Back-up Audit logs
- Retain audit trail history for 1 Year (minimum of 3 months immediately available)
Weekly
Perform critical file comparisons
Monthly
Install critical patches every month
Quarterly
- Delete stored chd
- Test for rogue wireless access point
- Run Internal & external vulnerability scans
3 months
Retain visitor log camera and/or access controls data storage
- Remove inactive user accounts 90 Days
- 15 minute system session idle time out
- 30 minute account lockout
- 90 days change passwords
- 4 passwords compare to history
- 7 characters in password
Annually
- Address new threats/vulnerabilities to public-facing web applications
- Perform internal and external penetration tests
- Review service provider compliance status
- Review and update the information security policy
- Provide PCI & security training to staff
- Document acknowledgment of policies/procedures
- Review & test incident response plan
- Verify equipment & media inventory
- Review security of stored media locations
- Perform risk assessment
Any questions? submit a helpsu ticket
Visit pcicompliance.stanford.edu
