How to Configure a Built-in VPN Client for Linux
The Cisco AnyConnect VPN client for Linux is recommended. The following instructions are provided for those who prefer to use a built-in VPN client for Linux. Please note that while native OS VPN connectivity is not officially supported, the instructions below are provided as a courtesy and the installation steps and/or procedure will vary depending on the chosen Linux distribution.
If you require additional support, please contact your local IT group.
Overview
Stanford's VPN allows you to connect to Stanford's network as if you were on campus, making access to restricted services possible.
Two types of VPN are available:
- Stanford (split-tunnel). When using Stanford's VPN from home, we generally recommend using the Stanford split-tunnel VPN. This routes and encrypts all traffic going to Stanford sites and systems through the Stanford network as if you were on campus. All non-Stanford traffic proceeds to its destination directly.
- Stanford-Full (non-split-tunnel). This encrypts all internet traffic from your computer but may inadvertently block you from using resources on your local network, such as a networked printer at home. If you are traveling or using Wi-Fi in an untrusted location like a coffee shop or hotel, you may wish to encrypt all of your internet traffic through the Stanford-Full non-split-tunnel VPN to provide an additional layer of security.
You can select thy type of VPN you want to use each time you connect to the Stanford VPN.
Install the OpenConnect client
- On Debian-compatible distributions (including Ubuntu), install the network-manager-openconnect-gnome package.
- On RedHat-compatible distributions (including Fedora and CentOS), install NetworkManager-openconnect-gnome.
Set up a new VPN interface
- In System Settings, open the Network panel and click the + button to create a new interface.
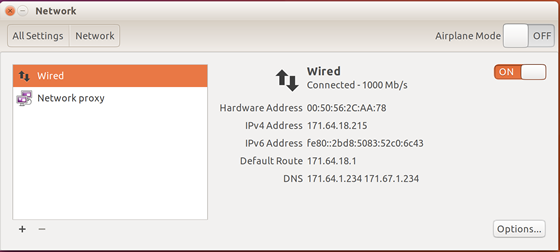
- On Ubuntu, select VPN from the list of interface types and click Create.
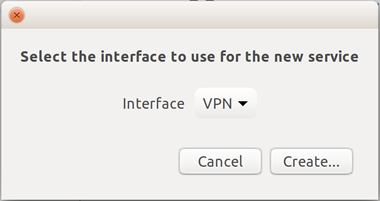
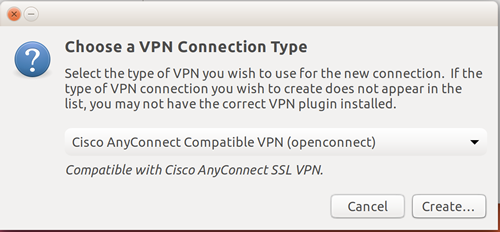
- Select the Cisco AnyConnect Compatible VPN connection type (and, on Ubuntu, click Create).
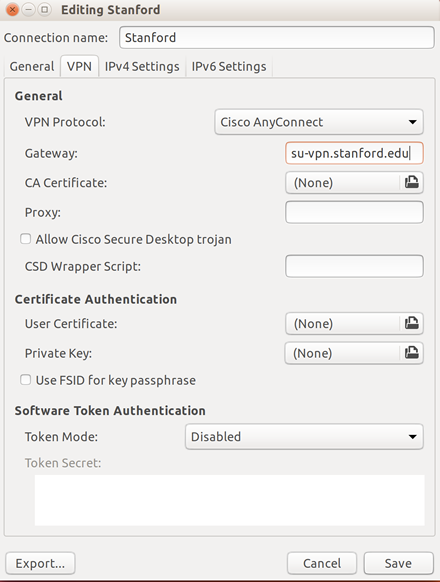
- Choose a name for the connection (e.g., Stanford) and set the Gateway to su-vpn.stanford.edu. Then, click Add (or Save).
Connect to the Stanford VPN (GUI)
- In the Network panel, turn the new interface on.
- On Ubuntu, in the System menu you may also click the Network icon select the new interface from the list of VPN Connections.
- On Fedora, in the System menu you may choose VPN Off and click Connect.
In the Connect to VPN dialog box, enter the following information and then click Login.
- GROUP: select Default Stanford split- tunnel or Full Traffic non-split-tunnel
- Username: your SUNet ID
- Password: your SUNet ID password
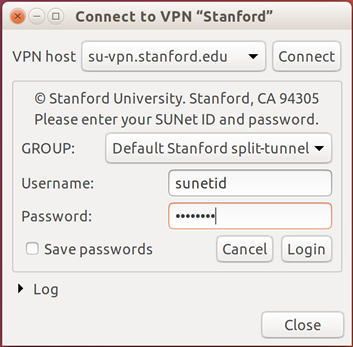
- Complete the two-step authentication.
Connect to the Stanford VPN (cli/shell)
open up a terminal/shell window and run the following command, replacing "sunetid" with your SUNet ID:
sudo openconnect --useragent=AnyConnect --no-external-auth --authgroup="Stanford" --user=sunetid su-vpn.stanford.eduauthgroup can be set to either "Stanford" or "Stanford-Full"
you should see output similar to this:
user@device:/tmp$ sudo openconnect --useragent=AnyConnect --no-external-auth --authgroup="Stanford" --user=sunetid su-vpn.stanford.edu POST https://su-vpn.stanford.edu/ Connected to 171.66.1.252:443 SSL negotiation with su-vpn.stanford.edu Connected to HTTPS on su-vpn.stanford.edu with ciphersuite (TLS1.3)-(ECDHE-SECP256R1)-(RSA-PSS-RSAE-SHA256)-(AES-256-GCM) Got HTTP response: HTTP/1.0 302 Temporary moved POST https://su-vpn-press.stanford.edu/ Connected to 171.66.1.253:443 SSL negotiation with su-vpn-press.stanford.edu Connected to HTTPS on su-vpn-press.stanford.edu with ciphersuite (TLS1.3)-(ECDHE-SECP256R1)-(RSA-PSS-RSAE-SHA256)-(AES-256-GCM) XML POST enabled Please enter your username and password. POST https://su-vpn-press.stanford.edu/ XML POST enabled Please enter your username and password. Password: POST https://su-vpn-press.stanford.edu/ At the Password prompt, enter a two-step code or an option # (1-3) from below: 1. Push to X-1234 2. Call to X-1234 3. Text to X-1234 Response: POST https://su-vpn-press.stanford.edu/ Got CONNECT response: HTTP/1.1 200 OK CSTP connected. DPD 300, Keepalive 20 Established DTLS connection (using GnuTLS). Ciphersuite (DTLS1.2)-(ECDHE-RSA)-(AES-256-GCM). Configured as 10.130.17.29, with SSL connected and DTLS connected Session authentication will expire at Wed Jul 23 15:05:01 2025 ignoring non-forwardable exclude route 0.0.0.0/32 Using vhost-net for tun acceleration, ring size 32To terminate the connection, use ^C:
^CSend BYE packet: Aborted by caller User cancelled (SIGINT/SIGTERM); exiting.*** Please note that when prompted to enter a number for two-step authentication (1-3), that number will not be echoed to the screen. Press the number that corresponds to the option you'd like to use and then press enter.
